One of the recurrent problems for partners and other service providers supporting Microsoft 365 customers is the allocation of access permissions that enable the partner to work on the customer’s systems and services on their behalf. A feature called delegated administration privileges (DAP) has long made that possible, but DAP grants the partner full Global Admin privileges over the customer’s tenancy.
Many customers might be hesitant to grant those privileges, and rightly so; if the partner’s systems become compromised, then the customer could also be compromised—as could all the partner’s other customers. Also, when the partner has multiple people working on a customer’s network, all using the same Administrator account, it can become difficult to maintain accountability for the changes made. These are vulnerabilities that can be a dealbreaker for a partner/customer relationship.
Granular delegated admin permissions (GDAP) is a revision of DAP that enables partners to assign more specific Entra ID permissions to their users, fulfilling the least-privilege requirement of the Zero Trust initiative. Partner personnel managing the customer’s Azure subscriptions—such as creating and configuring users—are made members of an Admin Agent security group that grants them the privileges they need, as shown in Figure 3-43.
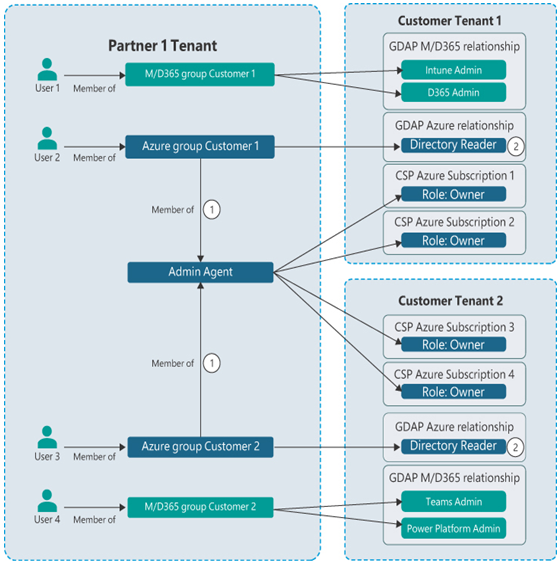
FIGURE 3-43 GDAP partner/customer relationships
Follow these steps to assign GDAP privileges:
The partner first requests a relationship with the customer in the Microsoft Partner Center, which specifies a time limit for the privileges to be granted (with a two-year maximum) and the Entra ID roles the partner should be assigned.
The Partner Center generates an email containing the request and sends it to the customer.
Once the customer approves the request, the partner can use the Admin Relationships page in the Partner Center to create security groups and assign Entra ID roles to them.
In addition to entering into a different type of partner/customer relationship, GDAP also makes it easier for either party to terminate that relationship without manually denying privileges.
Describe Microsoft Purview and compliance solutions such as insider risk, auditing, and eDiscovery
For many IT professionals, the prospect of implementing vital services and storing important company information in the cloud is met with significant trepidation. They might have an instinctive reluctance to trust an IT infrastructure not implemented on computers the company owns and housed in their own datacenters. They might also hesitate to give up their control over those computers and their resources. Also, there might be statutes and standards to which the IT infrastructure must comply, whether because of contracted terms, company policies, or governmental requirements.







Leave a Reply