An endpoint is any device that connects to the network from any location, whether the device belongs to the company, an employee, or a guest user. Zero Trust calls for security policies to be applied and enforced uniformly on endpoints of all types by tools such as Microsoft Intune, regardless of the users’ identities or the devices’ locations. Devices have identities as well, which must be validated during every transaction.
If one of the two main innovations of Microsoft 365 is the use of cloud-based services, the other is the ability of users to access those services using many different types of devices that run on various computing platforms and work at any location with Internet access. As noted earlier, VPN connections have long enabled remote users to access the company network from home or while traveling, using a laptop or desktop. In subsequent years, there were a few mobile devices—nearly always supplied to users by the company—that were able to access a remote network but with limited utility, such as email only. Today, Microsoft 365 enables remote users working with desktops, laptops, tablets, and smartphones to access virtually any enterprise service or resource they could access using an on-premises workstation. However, the trick is to make this access possible while also making it secure.
Therefore, device security in Microsoft 365 must address two relatively new issues:
- Mobile devices that frequently operate outside of the organization’s protective perimeter
- The increasing use of BYOD mobile devices that are not selected and owned by the company
Because mobile devices can access any and all sensitive information maintained by the enterprise, there must be some means to protect that information from the threats to which all mobile devices are subject, including loss, theft, and misuse.
Endpoint security
While administrators can still use traditional access-control measures, such as file system permissions, to regulate who can work with the organization’s sensitive data, the Azure Active Directory and Microsoft Intune services are primarily responsible for ensuring that the devices used to access that data are safe. Microsoft 365 supports a large number of mobile computing platforms, including the following:
- Windows 10/11
- Android
- Android enterprise
- iOS
- macOS
The interaction between mobile devices and the Microsoft 365 cloud services is complex, as shown in Figure 3-41. However, as you can see in the diagram, Microsoft Intune functions as a clearing house for many of these services and uses Entra ID for authentication and authorization.
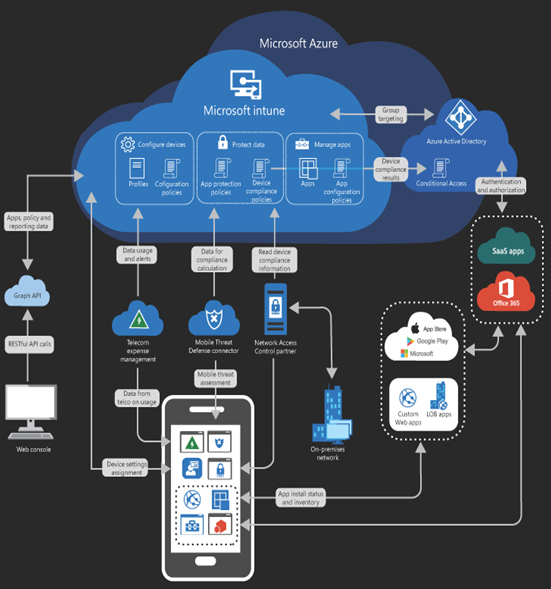
FIGURE 3-41 Microsoft Intune service architecture
Even when organizations have a BYOD (Bring Your Own Device) policy for their users’ endpoints, those devices must be subject to some form of enterprise endpoint security. This is the primary function of Microsoft Intune, which is Microsoft 365’s endpoint management tool; administrators use Intune to enroll users’ devices and exercise some degree of management on them. By creating health compliance policies using Intune, enrolled devices can be checked for adherence to those policies before Entra ID authorizes them to access enterprise services and information. This is known as conditional access. Because Entra ID and Intune operate in the cloud, they can control access to the other Microsoft 365 services from any location.







Leave a Reply