Once the data sensitivity and value have been assessed, the next step of the risk-management plan design process is to consider the technology used to store, access, transmit, and process that data. This includes the servers or cloud services where the data is stored when at rest, the client systems and devices used to access the data, the network components that carry the data between the various systems, and the applications that process the data.
In the same way that the data itself is inventoried in the previous phase, there should be an inventory of all the hardware involved in storing the data. This information can be used to locate the precise source of a security breach and to help prevent unauthorized devices from accessing secured company resources.
The primary storage locations for all sensitive company information should be servers in a secured environment, such as a datacenter or server closet, or a cloud service, which should have security policies detailed in the service contract. However, compiling an inventory of client systems and devices can be significantly more complicated. Workstations located at the enterprise sites are presumably already inventoried, but home computers and employees’ mobile devices, such as smartphones and tablets, need to be considered. Also, computers and devices belonging to people outside the organization, such as partners, consultants, temporary workers, and customers, need to be considered.
Administrators should document every device that comes into contact with company data. The inventory should include information such as the following:
- Make The manufacturer of the device
- Model The manufacturer’s model name and number for the device
- Serial number The manufacturer’s serial number for the device
- Owner The person or organization that is the owner of the device
- User The person or persons who use the device to access company data
- Location The place where the device is installed or, if mobile, the location of the person responsible for it
- Service ID The owner organization’s assigned ID number, if applicable
- Operating system The operating system installed on the device
- OS version The version and build of the operating system running on the device
- Network provider The provider used by the device to access the Internet or the company network
- Applications The applications on the device that are used to access company data
- Information used The specific types of company data that the device can access
For workstations owned by the organization, this information is typically compiled during the system’s deployment process and can probably be imported into the inventory. The information-gathering process should be required for systems and devices owned by employees before any access to sensitive company data is permitted.
Verifying inventory information can be difficult for frequent travelers or home computer users, but in the modern management model implemented by Microsoft 365, tight control of hardware devices is an essential element of enterprise security. For devices owned by people who are not employees of the organization, such as customers, the diplomatic aspects of enforcing these policies can be even more difficult. Still, administrators might be able to mitigate them by creating a risk level that provides these users with access only to a limited class of information that is not extremely sensitive.
In addition to the systems and devices that access company data, networking technology can also present an element of risk. The most obvious potential attack vector is wireless network devices, which are vulnerable to outside attacks in a variety of ways. Microsoft 365 includes Microsoft Intune, which enables administrators to create Wi-Fi network profiles that contain preshared keys and other security measures that prevent unauthorized devices from connecting to a company wireless network. Some extremely sensitive data types require special handling, even for wired networks, such as compliance regulations requiring network cables to be enclosed in sealed conduits to protect against wiretapping. Hardware-based security devices, such as firewalls, should also be included in the inventory.
When hardware that accesses sensitive information is compromised, the data is also presumed to be compromised. Administrators can use the hardware inventory to ensure that the operating systems and applications on the devices are updated with security patches and that antimalware and other security tools are updated. Administrators can also use Microsoft 365 tools to create compliance policies so that devices cannot access network resources unless they meet specific requirements, including up-to-date software.
The hardware security elements of a risk management plan can go beyond the capabilities of the tools in Microsoft 365. Protecting the hardware can include other mechanisms, including the following:
- Physical security Software-based security measures cannot fully protect the data stored on a computer if intruders have physical access to the machine. Even if the intruders can’t compromise the data, they can always destroy it, which can be just as damaging to the organization. Physical measures, even those as simple as a locked door, are basic elements of any risk management plan. For mobile devices, which are always vulnerable to loss or theft, administrators can use Microsoft Intune mobile device management to implement the ultimate hardware solution: remotely erasing the data from the device.
- High availability In addition to malicious or criminal intrusion, hardware devices are also liable to failures from wear and tear or destruction from natural disasters, such as fires, earthquakes, and extreme weather. High-availability measures, such as RAID arrays, redundant servers, and duplicate datacenters, can preserve data against loss and ensure that the data remains available to users. For Microsoft 365 data stored in the cloud, the Microsoft Global Network maintains datacenters worldwide, as shown in Figure 3-61, providing subscribers with a 99.9 percent availability rate.
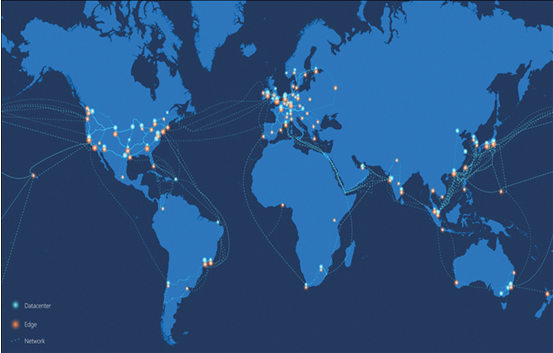
FIGURE 3-61 Microsoft Global Network datacenter locations
- Disaster recovery Data backups and cloud synchronization can enable sensitive data to be restored, even after an attack or a disaster renders the original data or the hardware on which it is stored unusable.







Leave a Reply