Small- and medium-sized businesses often lack IT personnel with a sufficient security background to manage and monitor the network using the tools provided in Microsoft 365. This creates a market for managed service providers (MSPs) who can lend their security expertise to their clients to help them protect their networks. Microsoft 365 Lighthouse is a cloud-based administration portal intended to provide MSPs with sufficient access to their clients’ networks security tools on their clients’ networks without giving away the keys to the kingdom.
Microsoft Lighthouse is based on a portal that enables MSPs to view all of their tenants’ networks in one place and focus on individual tenants, users, endpoints, and even threats. The tool can onboard new users and devices using security configuration baselines that the MSP can tailor to specific tenants.
Once onboarded, Lighthouse can track user activities and identify users at risk for security problems, as shown in Figure 3-35. The list identifies the users, provides their current status, and allows the MSP to select users to display more details about their risky behavior. The MSP can then take action by emailing the risky users, changing their passwords, requiring them to use multifactor authentication, or even preventing specific users from signing on.
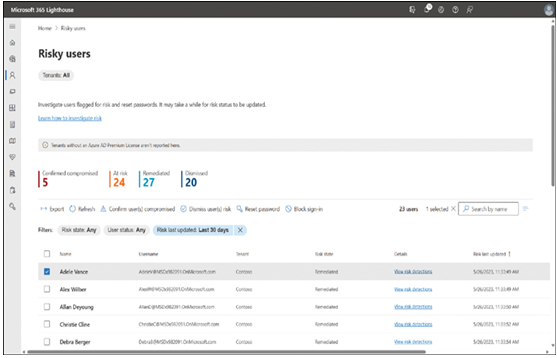
FIGURE 3-35 The Risky Users page in Microsoft 365 Lighthouse
Lighthouse enables MSPs to interact with their tenants from other directions as well. For example, instead of working with the users’ identities, an MSP can open the Threat Management page, shown in Figure 3-36 and display a list of all the threats detected on the tenants’ systems. MSPs can then work with individual threats and remediate all of their instances—on multiple users or even multiple tenants—at once.
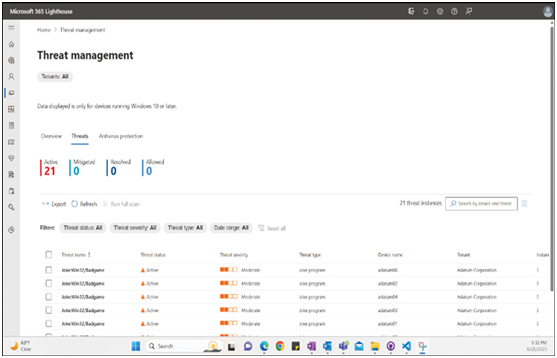
FIGURE 3-36 The Threats tab on the Threat Management page in Microsoft 365 Lighthouse
MSPs must be enrolled in Microsoft’s Cloud Solution Provider (CSP) program to manage their tenants with Microsoft 365 Lighthouse, but no additional costs are involved. There are no requirements for the tenants the MSPs are managing.
Skill 3.3: Describe trust, privacy, risk, and compliance solutions of Microsoft 365
Microsoft 365 includes a large number of security tools that work together in various ways to provide a network with trust, privacy, risk, and compliance solutions. Some of these solutions are discussed in the following sections.







Leave a Reply