Microsoft Purview includes auditing capabilities that log operations for many Microsoft 365 applications and services. Administrators can search the audit log directly from the Microsoft Purview portal, providing detailed information that can be useful during security, compliance, and legal investigations.
Microsoft Purview can provide two levels of audit logging, as follows:
- Audit (Standard) Standard auditing is enabled by default in Microsoft Purview, with logs that retain event entries for 90 days before deletion. Administrators can search the log from the Audit page in the Microsoft Purview portal, as shown in Figure 3-49, or by using the Search-UnifiedAuditLog cmdlet in Windows PowerShell.
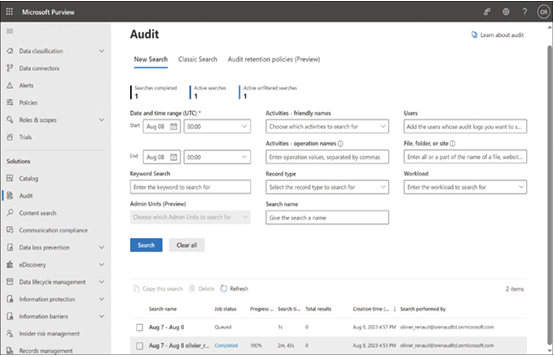
FIGURE 3-49 The Audit page in the Microsoft Purview portal
- Audit (Premium) Premium auditing stores Active Directory, SharePoint, Exchange, and OneDrive events for a full year, while retaining all other log entries for the standard 90 days. Administrators can also create their own log retention policies that extend the storage of logged events based on specific criteria, such as the service that generated the log entry. Audit (Premium) also provides intelligent insights into the logged information, making it more useful for investigations of security incidents.
eDiscovery
In addition to its auditing capabilities, Microsoft Purview includes a feature called eDiscovery, which is a tool for locating and packaging digital information for use as evidence in internal investigations, compliance efforts, and legal cases. eDiscovery can perform comprehensive searches across a wide range of Microsoft 365 data sources, as shown in Figure 3-50, including Exchange Online, SharePoint, Microsoft Teams, OneDrive, Microsoft 365 Groups, and Viva Engage. The tool can then export the search information and place a legal hold on the sources as needed.
FIGURE 3-50 The Locations page in the Microsoft Purview portal
eDiscovery is available in three versions, depending on the Microsoft 365 subscription level, as follows:
- Content Search Provides keyword search and export capabilities for Microsoft 365 data sources
- eDiscovery (Standard) Provides the same search and export capabilities as the Content Search option, plus the ability to create individual cases and assign custodians to them with exclusive access
- eDiscovery (Premium) Provides all the capabilities of eDiscovery (Standard), plus a complete end-to-end workflow and intelligent analytics that enable investigators to focus on the most relevant content
Describe how Microsoft supports data residency to ensure regulatory compliance
When people speak of storing data in the cloud, the implication is that the cloud is a single, unified resource on the Internet, which can store virtually unlimited amounts of data. This is not the case, however. Physically, the cloud is a series of datacenters in diverse locations. Different service providers have varying amounts of resources in various locations, but for Microsoft and the other large service providers, the cloud takes the form of hundreds of datacenters scattered around the planet.
Where a tenant’s data is located in the Microsoft cloud can be a critical factor, not only in the network’s performance of the network but also in the tenant’s compliance with any regulatory standards to which it is subject. From a performance standpoint, it is preferable for a tenant’s cloud data to be stored in a facility that provides the best possible performance. In some cases, the best location for a tenant’s data might simply be the nearest datacenter, but this is not always the case. Not all datacenters provide the same level of performance, so it might be possible for the best performance to be realized from a more distant facility.
Some tenants must comply with regulations regarding where and how they store their data, which can easily be a more critical factor in their data residency. Government contracts, educational institutions, and even some commercial client agreements might stipulate that data be stored in a certain place and way.
For example, U.S. government contracts might specify that data must be stored in a United States facility—or at least in a facility not located in a nation considered to be hostile. Some contracts might even forbid the use of cloud storage entirely and require a company to maintain its data in an on-premises datacenter.
For these reasons, it can be important for IT administrators to understand exactly where their data is going; “the cloud,” in these cases, is not a sufficiently detailed location.
When an organization creates a new tenant in the Microsoft Entra portal, it must select a location, as shown in Figure 3-51. Entra will create the tenancy in a datacenter located in the selected country. This location cannot be changed once the tenancy is created.
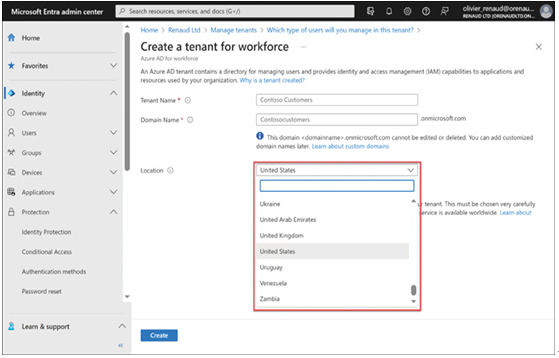
FIGURE 3-51 Selecting a location for a new tenancy in the Microsoft Entra admin center
For Microsoft tenants in the United States and other major countries, many datacenters support all of the Microsoft cloud services. However, not every country has datacenters that support all Microsoft 365 services. Exchange Online, SharePoint, and Microsoft Teams are available virtually everywhere. However, when a particular service is unavailable in a selected location, Microsoft will choose the nearest geographical location that supports it.
To see exactly where a tenant’s data is located for each Microsoft service, they can look at the Microsoft 365 admin center on the Org Settings page, under Organization Profile > Data Location, as shown in Figure 3-52.
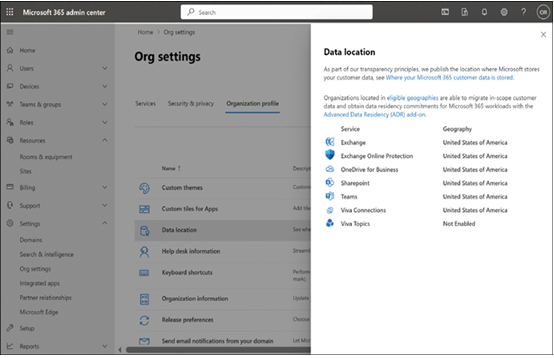
FIGURE 3-52 The Data location screen in the Microsoft 365 admin center
Describe information protection features such as sensitivity labels and data loss prevention
Microsoft 365 has various features that contribute to protecting the organization’s data, many of which have already been mentioned in this and the previous chapters. These features are discussed in the following sections.







Leave a Reply