Active Directory (AD) is a directory service that has been a part of the Windows Server product since the Windows 2000 Server release. A directory service is a database of objects, including users and computers, that provides authentication and authorization services for network resources. Authentication and authorization are essentially the front gates of information protection, providing basic, password-based security.
Microsoft Entra ID (formerly known as Azure Active Directory or Azure AD) is a cloud-based AD equivalent that can provide Microsoft 365 users with single-sign-on capability that enables them to access all their SaaS applications and services, including Microsoft 365 and any third-party products that administrators have integrated into their environment, from any device, at any location.
Entra ID provides a Microsoft 365 deployment with identity and access management services that extend beyond the on-premises network into the cloud. Entra ID enhances the security of the Microsoft 365 environment by supporting multifactor authentication, which requires users to verify their identities in two or more ways, such as with a password and a fingerprint or some other biometric factor.
Entra ID can also provide authentication and authorization services for internal resources, such as on-premises applications and services. For organizations with an existing Windows Server–based AD infrastructure, Entra ID can connect to internal domain controllers to create a hybrid directory service solution that shares the advantages of both implementations.
Microsoft Intune
As noted elsewhere, Microsoft Intune is a cloud-based device and application management tool that is integrated with the authentication and authorization functions provided by Entra ID. While administrators can use Intune to manage their in-house computers and applications, the primary innovation of the product is its ability to manage BYOD, or user-owned, devices, such as smartphones, tablets, and laptops, and enable them to access the organization’s protected services, applications, and data securely.
Intune can manage devices running any major mobile operating system, including Android, iOS, MacOS, and Windows. Using Intune, even operating systems that cannot join an Active Directory domain can access protected resources. Intune uses the mobile operating system’s protocols and APIs to communicate, building an inventory of devices that can access company applications and data.
Administrators can use Intune to create standards for configuring security settings that a device must meet before accessing protected resources. For example, an administrator can require that a device use a particular authentication type or specify that only certain applications can access company data. Intune can even ensure that sensitive data is removed from a device when an app shuts down. This type of control enables Microsoft 365 to maintain its resources’ security without administrators taking complete control over user-owned devices.
Azure Information Protection
Azure Information Protection (AIP) is a system that enables users and administrators to apply labels to documents and emails that classify the information they contain. The labels can be configured to specify how applications treat the information and, optionally, take steps to protect it.
AIP can apply labels to specific documents or follow rules created by administrators to identify sensitive data in any document. For example, an administrator can create a rule that identifies data patterns associated with credit card or Social Security numbers in a Word document as a user creates it. When the user attempts to save the document, AIP warns the user to apply the label, as shown in Figure 3-53.
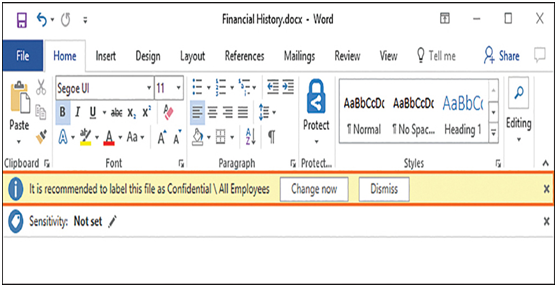
FIGURE 3-53 An AIP labeling recommendation in a Word document
Administrators can also configure AIP labels to be visible in the documents they are applied to. When a user agrees to classify a document as sensitive, the application can apply a watermark or other visual indicator, which will persist in the document wherever it is stored.
AIP can also use Azure Rights Management (Azure RMS) to protect documents or emails labeled as sensitive. Based on the rules created by administrators, documents labeled by AIP can be protected using encryption, identity restrictions, authorization policies, and other methods. For example, when an email message contains sensitive data, AIP can control the email client application, preventing users from clicking the Reply All or Forward button. Similarly, AIP can restrict Microsoft 365 documents to nonprinting or read-only status.







Leave a Reply