Risk management is a highly specialized undertaking heavily dependent on the type and sensitivity of the information to be protected and the nature of the threats to which the network is most vulnerable. For example, an organization that consists mostly of IT professionals will not be overly susceptible to phishing attacks because they have more awareness of them and experience with them. On the other hand, an organization of users with little or no IT expertise will be far more vulnerable to this particular threat and will require more effort to prevent this type of attack.
Microsoft 365 includes a wide variety of security tools that make it possible to predict, prevent, and react to many different kinds of threats. Many of these tools are discussed individually in this chapter and elsewhere in this book. The nature of each tool’s function is explained in relation to the types of threats it addresses. However, Microsoft recently announced an effort to organize Microsoft 365’s security components under the single name Microsoft 365 Defender, which places the tools into the following categories:
- Endpoints Tools that protect user devices and sensors from the effects of loss, theft, and attack, such as Microsoft Defender for Endpoint, Microsoft Intune, and Configuration Manager
- Cloud apps Tools that protect Software as a Service (SaaS) applications, such as Microsoft Defender for Cloud Apps and Exchange Online Protection
- Identities Tools that authenticate, authorize, and protect the accounts of standard users and privileged administrators, such as Microsoft Defender for Identity, Windows Hello, Azure Active Directory Identity Protection, and Privileged Identity Management
- User data Tools that analyze documents and messages for sensitive or malicious content, such as Microsoft Defender for Office 365, Exchange Online Protection, Azure Information Protection, and Data Loss Prevention
However, Microsoft 365 Defender is meant to be more than just a list of individual tools. Microsoft 365 Defender also gathers information from all these security components and accumulates them in a single Microsoft 365 Defender portal, as shown in Figure 3-29.
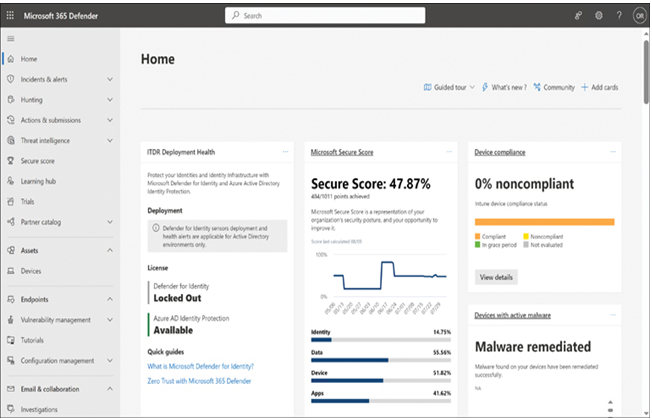
FIGURE 3-29 Microsoft 365 Defender portal
Microsoft 365 Defender goes beyond the reactive approach to security and provides tools that can be proactive by detecting attacks and other security issues before they occur or when they have barely begun. The various Defender tools are all designed to monitor the behavior of users, devices, and other network resources and analyze the information they collect to detect and anticipate suspicious behavior. The intelligence the tools apply to the task is based on the Microsoft Intelligent Security Graph, a web of security relationships that spans the entire network. Microsoft’s Cybersecurity Reference Architecture, shown in Figure 3-30, illustrates these relationships.
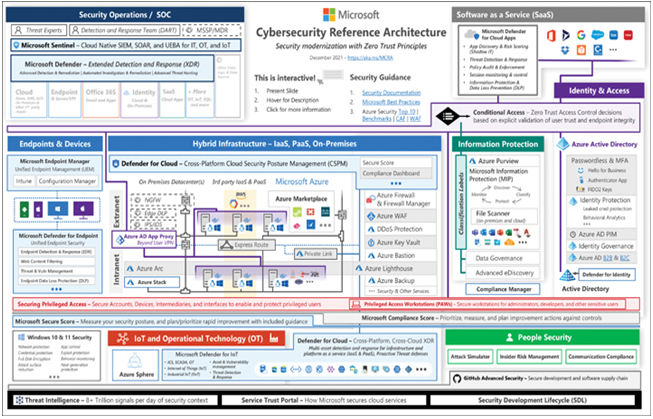
FIGURE 3-30 Microsoft Cybersecurity Reference Architecture
Need More Review? Microsoft Cybersecurity Reference Architecture
For an interactive PowerPoint version of the architecture shown in Figure 3-30, see https://aka.ms/MCRA.
The predominant threats to endpoints, applications, and identities are as follows:
- Endpoints Threats to endpoints can include various types of malware, including phishing attempts and ransomware. What often makes endpoints extra vulnerable, however, is when the devices are not compliant with the safety standards imposed by the management. Devices without the latest security patches or not protected by updated antivirus software can provide ingress to the network that attackers can exploit.
- Applications Shadow IT—the use of unauthorized applications—can leave a network open to a variety of attacks, including the introduction of malware or spyware to the network, as well as infrastructure attacks, such as Denial of Service (DoS) and Distributed Denial of Service (DDoS).
- Identities Credential theft is the chief threat against identities, which can take the form of social engineering, keystroke capture, and even brute force attacks.
A typical enterprise network today faces security threats from many directions and at many levels. Administrators must know that attackers frequently take advantage of vulnerabilities in an enterprise’s identities, documents, or endpoints. The following sections examine how the Microsoft 365 security tools address each area.







Leave a Reply