As shown in Figure 3-19, Microsoft 365 Defender treats security as though it’s divided into four domains: Identity, Endpoints, Apps, and Email/Collaboration Data. On many enterprise networks, the security operations for the four domains are separate, as each of them requires intense scrutiny. So, the people responsible for Identity security might not know about everything happening on the Apps security team.
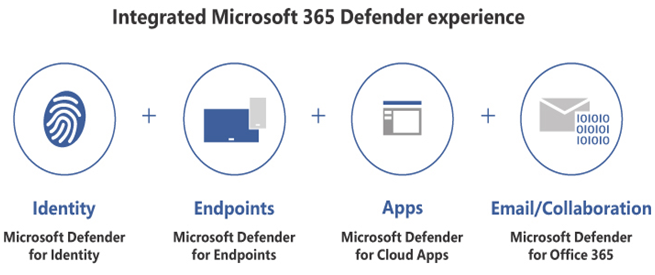
FIGURE 3-19 The Microsoft 365 Defender security domains
Many enterprises have separate security operations that each function within just one domain, or perhaps two, but none see the whole enterprise security picture. Attacks always begin in one of the four domains, but after gaining initial access to the network, attackers often move laterally between domains, rendering them partially invisible to single-domain detection procedures.
For example, an attacker might trick a user into revealing their password in an enterprise with domain-based security. This compromises the user’s identity and allows the attacker to access the network. The team responsible for identity security might recognize the attacker’s efforts, note the unauthorized access to the network, change the user’s password, and prevent such attacks from happening again, but that is the limit of their brief.
This is because once inside the network, the attacker might have used the stolen identity to take control of an application, thus moving laterally from the Identity domain to the Apps domain, as shown in Figure 3-20. The Apps security people might detect unauthorized access to the application, but they, too, are not fully aware of events outside their domain. This is not neglectful because the amount of incoming signal information to monitor in each domain is huge.
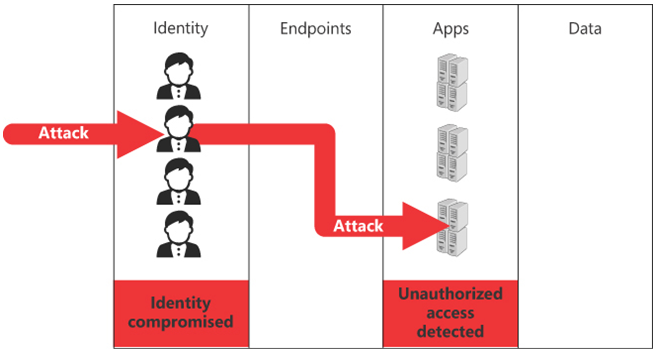
FIGURE 3-20 Lateral attack across security domains
The domain divisions mean nothing to an attacker, of course, but there will never be a complete picture of the current attack or future attacks unless the information gathered by the two separate teams—Identity and Apps—is collated and analyzed together, along with information from the Endpoints and Data teams.
This collation and analysis of information from all four domains is what the Microsoft 365 Defender suite is designed to do. Microsoft 365 Defender consists of a separate application for each of the four security domains, as follows:
- Microsoft Defender for Endpoint
- Microsoft Defender for Office 365
- Microsoft Defender for Identity
- Microsoft Defender for Cloud Apps
These separate applications all report to a central Microsoft 365 Defender engine that analyzes the input from the four domains and compiles a composite security picture that covers the entire enterprise infrastructure. Administrators can use the Microsoft 365 Defender portal to monitor and manage the ongoing security processes.
The following sections describe the capabilities of the Microsoft 365 Defender applications.







Leave a Reply