Microsoft Secure Score is a feature found in the Microsoft 365 Defender portal that displays a dashboard of the network’s overall security posture, as shown in Figure 3-26. Secure Score is designed to help administrators learn more about the inner security workings of their networks.
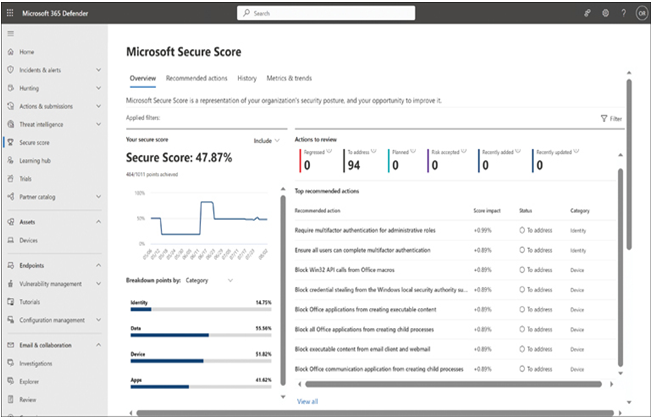
FIGURE 3-26 The Microsoft Secure Score Overview dashboard
The Secure Score is a percentage found in the upper-left corner of the dashboard that reflects the number of points administrators achieve by performing security-related tasks and enacting items from the list of recommendations provided by Microsoft 365 Defender.
Directly beneath the Secure Score is a series of graphs that break down the score by specifying how many points were achieved in each of the four standard security categories: identity, data, device, and apps. Next to the graphs is the list of recommendations provided by Microsoft 365 Defender for each of the four categories and each licensed application.
For example, the first recommendation in the list calls for requiring multifactor authentication during administrative sign-ins. Double-clicking the recommendation switches the Microsoft Secure Score display to the Recommended Actions tab and opens a sidebar with more information, as shown in Figure 3-27.

FIGURE 3-27 A recommended action in the Microsoft Secure Score dashboard
This particular recommendation states that it is worth a possible nine points or 0.89 percent of the Secure Score value. As administrators complete the recommended task according to the instructions on the Implementation tab, Defender adds the points to the score and recalculates the Secure Score value.
Some tasks have binary solutions; an administrator either completes the task or does not and receives all or none of the points. In recommendations like this one, however, Defender awards partial points for partially completed tasks. It is also possible for the network to lose points and for its score to regress, such as when additional users who suffer from a security condition and are already recommended for remediation are added to the network.
Secure Score is not intended to be a set of instructions that administrators must follow by rote. Every enterprise network has its own needs and peculiarities, so there might be some recommendations that are not practical or possible in a specific situation.
For example, Defender might add the Block Win32 API calls from Office macros recommendation to a Secure Score page because it can help to prevent malicious code from being introduced into the network. However, if the network has users that require those API calls to do their jobs, then the administrators can create an exception like the one shown in Figure 3-28, indicating that they are willing to accept the risk or that they have some other means of preventing macro intrusions in place.
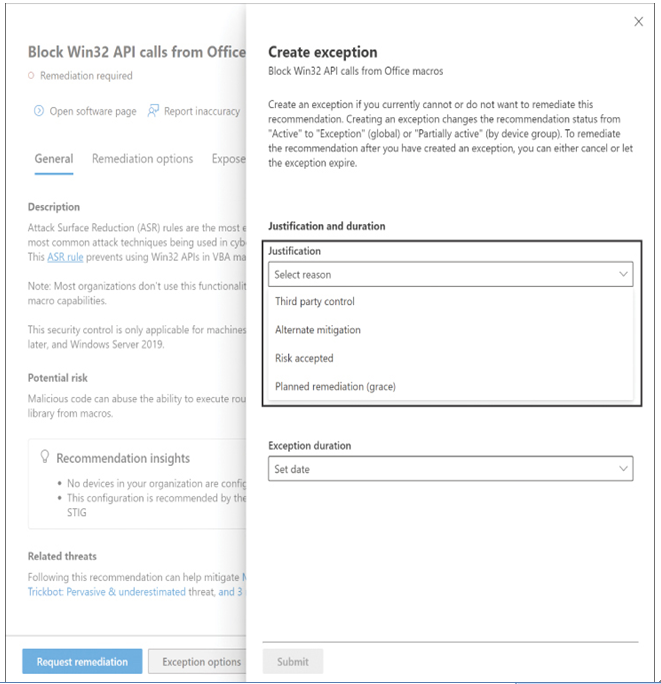
FIGURE 3-28 Creating an exception in the Microsoft Secure Score dashboard







Leave a Reply