Microsoft Defender for Cloud Apps is a cloud access security broker (CASB), essentially an intermediary between Microsoft 365 cloud users and the cloud-based Software as a Service (SaaS) apps they run. Like the other Defender products, the administrative interface for Defender for Cloud Apps has been integrated into the Microsoft 365 Defender portal.
Defender for Cloud Apps monitors the apps the network users are accessing to ensure that the apps are authorized and used safely. The product includes the main features shown in Figure 3-23:
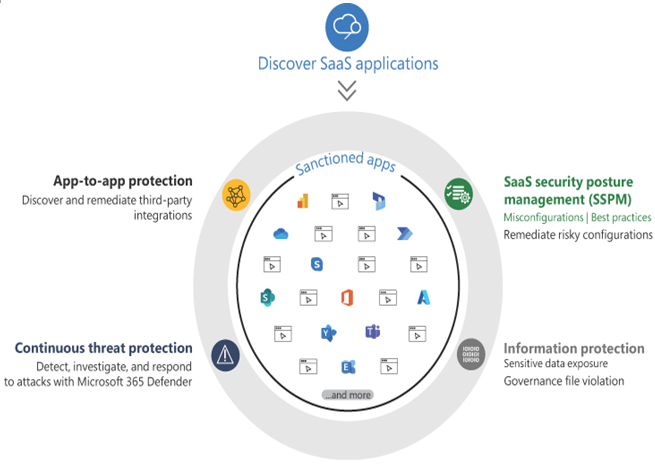
FIGURE 3-23 Microsoft Defender for Cloud Apps features
- Cloud app discovery Defender for Cloud Apps uses network traffic analysis and other techniques to perform a pattern search in the Microsoft cloud app catalog of 25,000 applications. After identifying all of the cloud apps being used on the network, Defender then assesses each app as a potential threat based on more than 90 risk factors and displays the resulting information in a dashboard like the one shown in Figure 3-24. Administrators can selectively sanction the apps they want users to access while desanctioning those they do not.
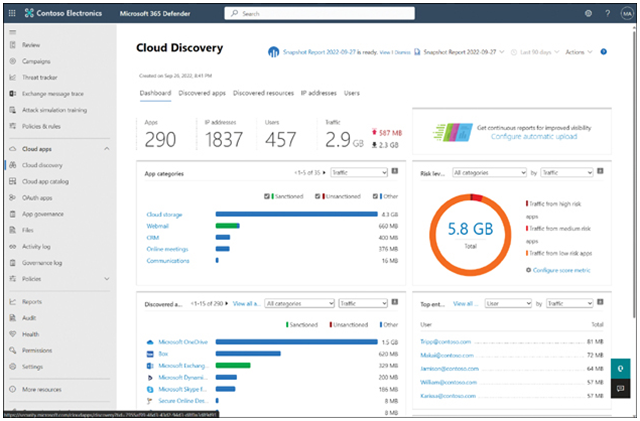
FIGURE 3-24 The Cloud Discovery dashboard in the Microsoft 365 Defender portal
- SaaS security posture management Every SaaS app is different, and administrators often cannot practically learn the configuration peculiarities of dozens or hundreds of sanctioned apps. Defender for Cloud Apps, using the information in the cloud app library, compares the best practices for each app with its current configuration settings and generates recommendations for revised settings and actions. Defender for Cloud Apps supports using APIs supplied by the cloud application providers for sanctioned applications. These APIs enable Defender to function as an intermediary between cloud applications and the enterprise’s users, as shown in Figure 3-25, by accessing activity logs, user accounts, and data sources. Defender for Cloud Apps can then use this information to monitor usage, enforce policies, and detect threats.
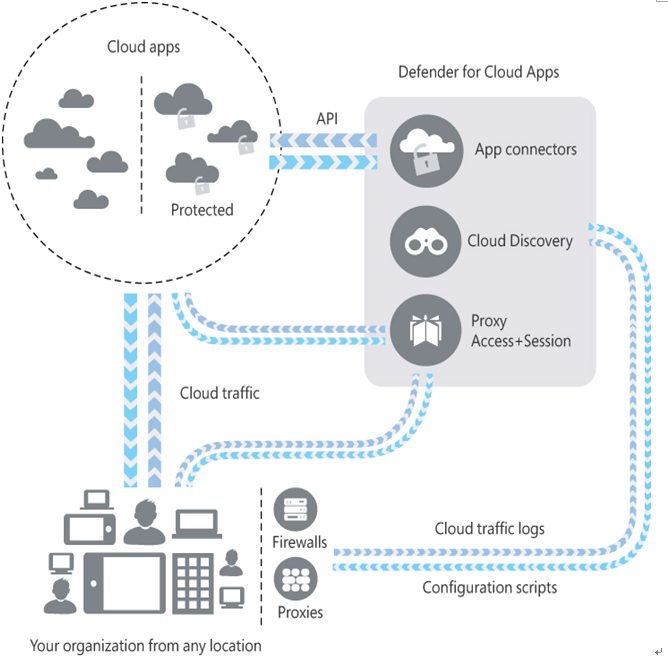
FIGURE 3-25 Interactions of Defender for Cloud Apps with an enterprise network and cloud applications
- Information protection Defender for Cloud Apps is integrated into the Microsoft 365 Data Loss Protection (DLP) engine, which enables Defender to scan cloud apps for sensitive data, log its location and who is accessing it, and take actions such as applying a label or even blocking user access.
- Continuous threat protection As noted earlier, Defender for Cloud Apps is integrated into Microsoft 365 Defender, which makes it part of the high-level Microsoft 365 security posture, continuously monitoring cloud app alerts and integrating them into the enterprise attack investigations.
- App-to-app protection Open Authorization (OAuth) is a standard that enables one app to access information on another app on a user’s behalf. This is naturally a security concern, and Defender for Cloud Apps can add help by adding protection to the app-to-app communications with application governance. Application governance takes the form of policies that determine how apps communicate with each other, as well as actions and alerts that can remediate problem situations.







Leave a Reply