As mentioned frequently in this book, an organization’s data is its most valuable commodity, and keeping that data secure is one of the primary functions of Microsoft 365. That company data frequently includes confidential information, however, and it is the responsibility of the IT department not only to keep the data secure but also to maintain its privacy.
Microsoft Priva is a tool that helps administrators establish and maintain the privacy of the company’s data in light of the many regulatory laws about data privacy now in place in the U.S. and other countries. Priva is not concerned with protecting data against outside attacks; other Microsoft 365 tools handle that. Regarding data privacy, Priva is concerned mainly with how the organization handles its sensitive data internally.
Microsoft Priva consists of two privacy solutions, as follows:
- Priva Privacy Risk Management Uses built-in or custom policy templates to identify data that is subject to privacy risks, generates alerts when data conforming to a policy is detected, and provides administrators with the ability to investigate and remediate the alerts
- Priva Subject Rights Requests Simplifies and automates the process of responding to legally submitted data subject requests by prioritizing data, implementing workflows, and generating reports
The first task undertaken by Priva is to identify the personal data stored by the company that is at risk. The Priva administration interface is included in the Microsoft Purview portal under the Privacy Management menu. The Overview dashboard, shown in Figure 3-55, specifies the number of items containing personal data and the number of outstanding rights requests. The Overview dashboard also displays key insights into the discovered personal data and a list of the current action policy alerts.
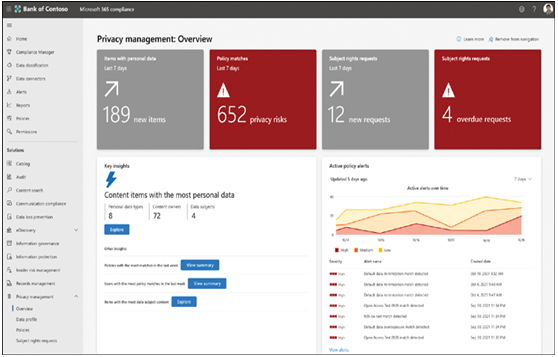
FIGURE 3-55 The Microsoft Priva Privacy Management: Overview page
Priva risk management
Once Priva has identified the data stored by an organization, administrators can select a template to create a policy that will govern the data handling. Priva includes templates to address the following privacy risks:
- Data overexposure Data that is publicly available, shared too widely within the organization, or shared with individuals outside the organization. Prevalence of this type of risk should compel administrators to educate users about data-sharing policies.
- Data transfers Creates policies that detect when data is transferred in an unsafe manner, as determined by the administrator. Depending on the type and sensitivity of the data, administrators can limit unencrypted transfers between departments, geographic locations, or individuals outside of the organization.
- Data minimization Potentially sensitive data that has been stored unused for a long period of time can present unnecessary risks. This template can create policies that identify such data and notify its owners to use or delete it.
The Policies page in the Microsoft Purview portal allows administrators to create a new data transfers policy, as shown in Figure 3-56, or create a new custom policy from scratch.
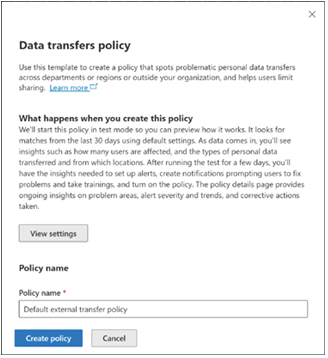
FIGURE 3-56 Creating a data transfers policy in Microsoft Priva







Leave a Reply