Advanced Threat Analytics (ATA) is an on-premises solution that uses information gathered from a wide variety of enterprise sources to anticipate, detect, and react to security threats and attacks. ATA receives log and event information from Windows systems and also captures network traffic generated by security-related protocols, such as Kerberos and NTLM. This traffic provides ATA with information about user authentication and authorization patterns.
Using this gathered information, ATA builds up profiles of applications, services, and users. By examining the normal behavior of these entities, ATA can detect anomalous behavior when it occurs and ascertain whether that behavior is suspicious based on known attack patterns. When it suspects or detects a security breach, ATA displays an alert in the ATA dashboard, such as the one shown in Figure 3-54.
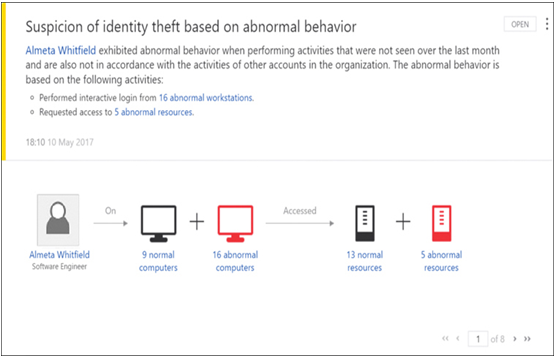
FIGURE 3-54 A Microsoft Advanced Threat Analytics alert to abnormal behavior
ATA is one of several Microsoft 365 technologies that uses advanced intelligence to anticipate user needs before they occur. In this case, the need is for intervention, whether automated or human, in a potentially dangerous security situation.
Microsoft Defender for Cloud Apps
Microsoft’s research has determined that many of the hundreds of cloud applications that large enterprises use today are unknown to the IT department and therefore are unmanaged by them. Microsoft has started calling these clandestine cloud apps shadow IT, and they obviously present a security hazard.
Microsoft Defender for Cloud Apps (formerly called Cloud App Security) is a cloud access security broker (CASB) product that enables Microsoft 365 administrators to scan their networks for the cloud apps that users are accessing, assess their security vulnerability, and continuously manage them.
Defender for Cloud Apps examines traffic logs and firewall and proxy information to discover the cloud apps in use. After determining whether the apps are dangerous to data, identities, or other resources, administrators can sanction or unsanction specific apps to allow or prevent user access to them. For apps administrators have sanctioned, Defender uses their own APIs to connect to them and monitor user activity.
Microsoft Defender for Identity
As with the Microsoft Defender Advanced Threat Protection feature included in Windows 10, Microsoft Azure has its own ATP, as do Office 365, Exchange Online, SharePoint, Microsoft Teams, and OneDrive. However, Azure Advanced Threat Protection is now known as Microsoft Defender for Identity. Each ATP engine is designed to use machine intelligence to prevent, detect, and respond to the security threats unique to its environment. In Azure, the primary vulnerability is the identities stored in Entra ID (Azure Active Directory), so the Azure ATP engine looks for anomalous user behavior and compares it to standardized patterns used by attackers.
Azure Information Protection is included in all the Microsoft 365 plans, but it is also available with other Microsoft products in a free version with limited functionality and as a separate subscription in two plans of its own, called Premium P1 and Premium P2. Each subscription level adds features, as shown in Table 3-4, and includes all the features of the lower subscription levels.
TABLE 3-4 Azure Information Protection subscriptions
| Plan | Included with | Description |
| Free | No purchase necessary | Allows consumption of AIP-protected content by users with accounts that are not associated with Azure identities |
| Azure Information Protection for Office 365 | Office 365 Enterprise E3 and above | Provides protection for Office 365 services using custom templates and supporting Office 365 Message Encryption |
| Azure Information Protection Premium P1 | Microsoft 365 Business Microsoft 365 Enterprise E3 Microsoft Enterprise Mobility + Security E3 | Provides the ability to use on-premises connectors, track and revoke documents, and manually classify and label documents |
| Azure Information Protection Premium P2 | Microsoft 365 Enterprise E5 Microsoft Enterprise Mobility + Security E5 | Provides support for policy-based rules and automated classification, labeling, and protection of documents |







Leave a Reply