Endpoints are the devices connected to a network: computers, smartphones, tablets, wireless access points, routers, and firewalls. All endpoints are potential points of vulnerability, and Microsoft Defender for Endpoint is designed to discover, configure, and monitor these endpoints. Defender for Endpoint can also remediate the issue when it detects suspicious behavior.
As with all of the Microsoft 365 Defender products, management of Defender for Endpoint is integrated into the Microsoft 365 Defender portal. Microsoft Defender for Endpoint is available in two plans, plus an add-on for Plan 2, as shown in Table 3-2.
TABLE 3-2 Microsoft Defender for Endpoint products
| Defender for Endpoint Plan 1 | Defender for Endpoint Plan 2 | Defender Vulnerability Management add-on for Plan 2 |
| Next-generation antivirus and antimalware protection | All Defender for Endpoint Plan 1 features | All Defender for Endpoint Plan 2 features |
| Attack surface reduction | Device discovery and inventory | Security baselines assessment |
| Manual response actions | Vulnerability management | Blocking of vulnerable applications |
| Centralized management | Threat analytics | Hardware and firmware assessment |
| Security reports | Automated investigation and response | Network share analysis |
| Support for Windows 10, Windows 11, iOS, Android OS, and macOS devices | Endpoint detection and response | Authenticated scan for Windows |
Microsoft 365 Enterprise E3 includes Plan 1, and Enterprise E5 includes Plan 2. Mixed licensing scenarios are available, in which a tenancy includes both Plan 1 and Plan 2 clients. There is also a standalone Microsoft Defender for Business product, designed for networks of up to 300 users, which includes many of the Defender for Endpoint features found in Plans 1 and 2.
Defender for Endpoint provides tools for investigating endpoint security threats, including the following:
- Vulnerability management Defender for Endpoint continuously monitors the network (as shown in Figure 3-21), inventories hardware and software components such as certificates and browser extensions, discovers potential vulnerabilities, assesses their associated risks, and remediates them.
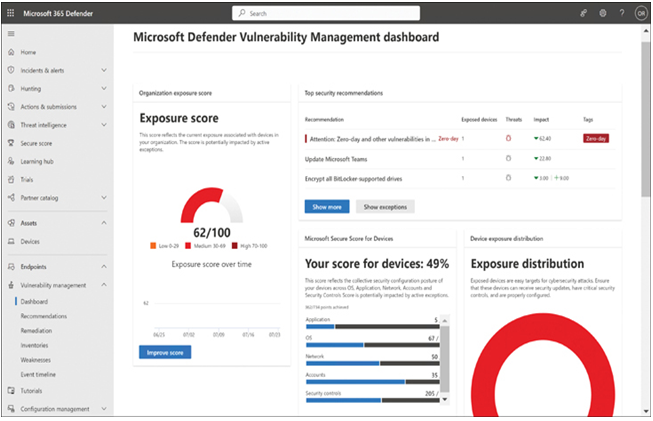
FIGURE 3-21 Microsoft Defender Vulnerability Management dashboard
- Attack surface reduction Minimizes the attack risk by restricting users to only the resources they need. Using zero trust principles, attack surface reduction allows administrators to designate applications as trusted and specify folders that only trusted applications can access. In the same way, network protection prevents endpoints from communicating with websites suspected of hosting malware, phishing attempts, and other suspicious behaviors.
- Endpoint detection and response Provides near real-time detection of attacks, generating alerts that it incorporates into incidents describing similar threats. This enables administrators to analyze security events based on evidence gathered over time.
- Automated investigation and remediation After generating alerts, Defender for Endpoint initiates an investigation by scanning its records for similar occurrences on other systems and using artificial intelligence. Defender executes remediations based on automation levels configured for machine groups, as follows:
- Not protected Turns off all remediation.
- Semi Requires administrator approval for particular types of remediation.
- Full Performs remediations automatically.
- Endpoint attack notifications Formerly known as Microsoft Threat Experts, Defender proactively hunts for common threats and generates alerts when it finds them.
Microsoft Defender for Office 365
Microsoft Defender for Office 365 is designed to provide protection from attacks arriving through email messages, web links, and Microsoft 365 collaboration tools, including Microsoft Teams, SharePoint, and OneDrive. While all accounts using Microsoft Exchange Online for email are protected by Exchange Online Protection (EOP) against spam, phishing, and malware attempts, Microsoft Defender for Office 365 includes more extensive protection, including the ability to interact with the main Microsoft 365 Defender engine.
Microsoft Defender for Office 365 is available in two plans, as shown in Table 3-3. Plan 1 includes more extensive malware, phishing, email attack detection capabilities; Plan 2 goes beyond the real-time detection of email and collaborative documents and adds automated attack investigation, threat hunting, and attack simulators that administrators can use for training purposes.
TABLE 3-3 Microsoft Defender for Endpoint products
| Defender for Office 365 Plan 1 | Defender for Office 365 Plan 2 |
| Safe attachments | All Plan 1 features |
| Safe links | Threat trackers |
| Safe attachments for SharePoint, OneDrive, and Microsoft Teams | Threat Explorer |
| Anti-phishing protection | Automated investigation and response (AIR) |
| Real-time detections | Attack Simulator |
| Advanced hunting | |
| Microsoft 365 Defender integration |
Microsoft 365 Enterprise E5 includes Plan 2, but for other Microsoft 365 subscriptions, Defender for Office 365 must be purchased as a standalone subscription.







Leave a Reply