Self-service password reset (SSPR) is a feature in Azure Active Directory that enables users to reset their own forgotten passwords, change their existing passwords, and unlock their accounts when they have been frozen. This can significantly reduce routine trouble calls without sacrificing identity security.
Before users can reset their own passwords, administrators must enable SSPR in the Microsoft Entra admin center, as shown in Figure 3-14. The interface allows administrators to enable self-service password reset for all users or selected ones.
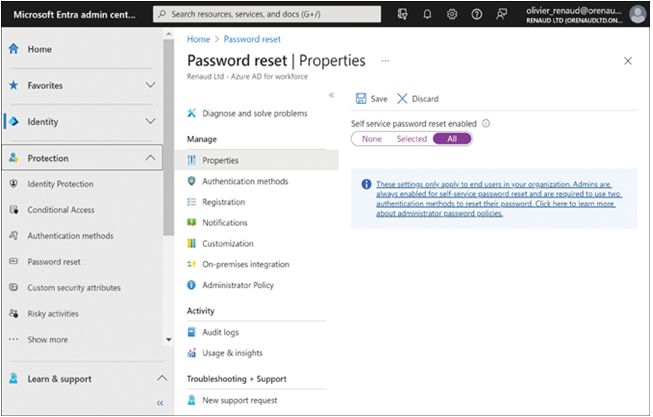
FIGURE 3-14 The Password Reset | Properties screen in the Microsoft Entra admin center
The next time users log on after SSPR is enabled, a screen appears, prompting them to register by selecting the authentication methods they will use during the password reset or downloading the Microsoft Authenticator app, as shown in Figure 3-15.
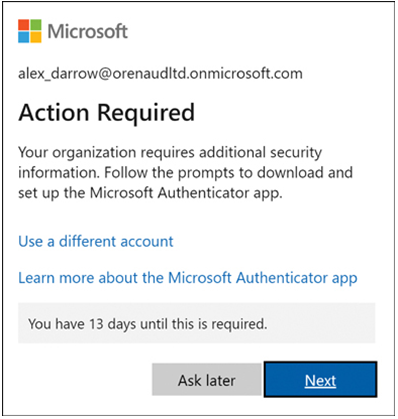
FIGURE 3-15 The Action Required pop-up window
Conditional access
Conditional access is an Entra ID feature that enables administrators to create policies that control user access to applications and data based on a variety of conditions. Entra ID processes conditional access policies after the user’s first authentication factor.
When processing conditional access policies, Entra ID analyzes information about the user, the user’s device, the device’s location, the applications on the device, and the degree of risk associated with the protected resources, as shown in Figure 3-16. Based on this information, Entra ID might allow or deny the user access to the resource, require the user to complete additional authentication factors or even switch to a more compliant device.
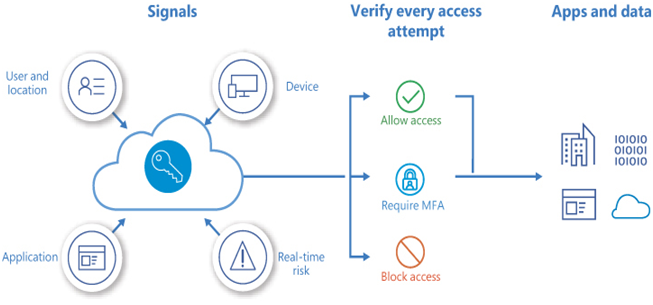
FIGURE 3-16 The conditional access verification procedure
The conditional access assessment is essentially an if/then statement that balances the incoming signals with a series of possible outcomes. For example, when a user attempts to access a particular application, a conditional access policy might evaluate signals such as the following:
- If the user is connected to the on-premises network
- If the user completes their first authentication successfully
- If the user is a member of a group granting permissions for the application
- If the user is working on a device with adequate malware protection
If the user meets all of these requirements, the conditional access policy processes the Then parts of the statement:
- Then the user must complete the second factor of a multifactor authentication
- Then the user is granted access to the application
Administrators can use the Microsoft Entra admin center to create conditional access policies, as shown in Figure 3-17. The Conditional Access page includes templates for creating policies, such as Require Multifactor Authentication For A dmins, or it is possible to create an entirely new policy.
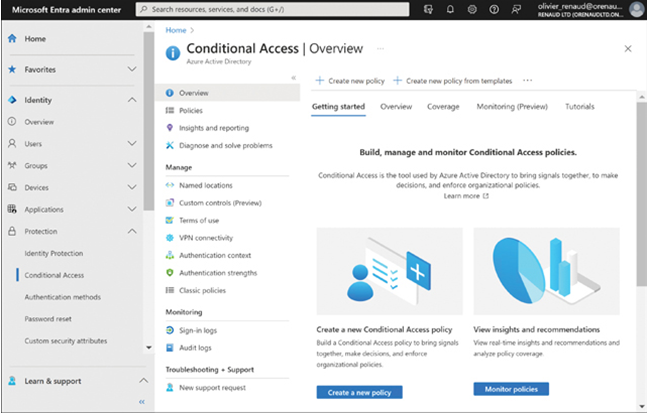
FIGURE 3-17 The Conditional Access screen in Microsoft Entra admin center
When creating a new conditional access policy using the interface shown in Figure 3-18, administrators can configure the following elements:
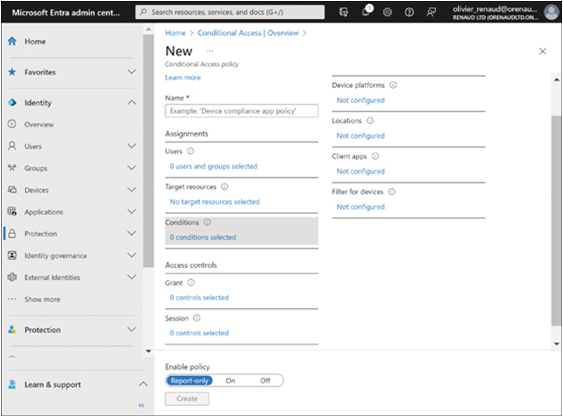
FIGURE 3-18 The Conditional Access screen in Microsoft Entra admin center
- Users Specifies the users and groups to which the policy will apply
- Target Resources Identifies the cloud apps or other protected resources to which the policy applies
- Conditions Specifies the conditions the user must meet to be granted access, such as the following:
- Device Platforms Specifies the allowed platforms for the user’s device, such as Windows, macOS, Android, and iOS
- Location Specifies the allowed physical locations for the user
- Client Apps Specifies the client applications in which the user will be allowed to work
- Filter For Devices Includes or excludes devices from the policy based on the values of specific device properties
- Grant Specifies whether user access to the target resources should be blocked completely or granted with one or more conditions, such as the need for a password change, multifactor authentication, or a hybrid Entra ID-joined device
- Session Specifies session limitations for specific apps, such as how long a user’s access persists before reauthentication is necessary and whether browser sessions are persistent
Selecting the On option in the Enable Policy selector activates the policy and applies it as configured.
Quick check
- Which of the following elements creates hybrid identities by replicating on-premises identities to the cloud?
- Entra ID
- Azure AD Connect
- Password hash synchronization
- AD DS
Quick check answer
- Azure AD Connect is a software tool that runs on the on-premises network and replicates Active Directory domain Services identities to Azure Active Directory in the cloud, creating hybrid identities.
Skill 3.2: Describe threat protection solutions of Microsoft 365
Originally, Windows Defender was the name of Microsoft’s antivirus feature for Windows XP. Now called Microsoft Defender Anti-Virus, that feature still exists in Windows 10 and 11. However, the brand has grown, and Microsoft 365 Defender is now the name of a unified protection suite that detects, isolates, and remediates threats wherever they occur in the Microsoft 365 infrastructure.







Leave a Reply